>WIFI_HACKING_
Getting Started w/ Terms & Technologies

WiFi is something that we all use every single day. Do you ever think about the risks
whenever you connect to someone else's WAP (Wireless Access Point) on the day to
day?
I'm going to cover a few attacks that can happen over a wireless network, but first..
How do you get started in hacking wifi?
Terminology
To really understand how to hack Wi-Fi, we need to dispense with basic terms and technology. First, let's address some terminology.To begin, the access point that sends out the radio frequency (RF) signal is known as the AP. These APs are capable of sending out signals (between 2.4 and 5 Ghz) that comply with a number of different standards. These standards are known as 802.11a, 802.11b, 802.11g, and 802.11n. In the very near future, we'll see a new standard that's tentatively named 802.11ac.
The table below summarizes the key features of these Wi-Fi standards.
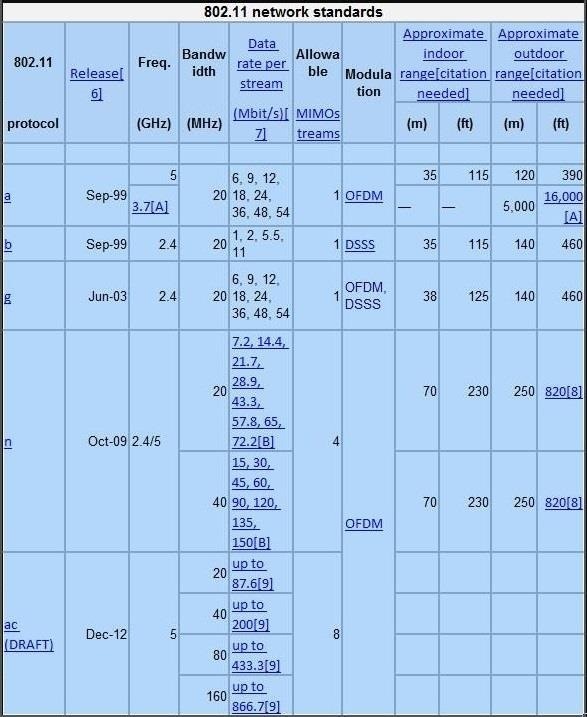
These standards are generally backwardly compatible, so that a wireless n adapter will also be able to pick up g and b signals. We will focus upon the most widely used of these standards— b, g, and n.
Security Technology
From the perspective of the hacker, wireless security technologies are among the most pertinent
features. Multiple security technologies
have been deployed in Wi-Fi to make an inherently insecure technology secure.
Our attack
approach will depend upon which of these security technologies is being deployed.
So, let's take a quick look at them here.
- WEP -
WEP, or wired equivalent privacy, was the first wireless security scheme employed. As it name
implies, it was designed to
provide security to the end-user that was essentially equivalent to the privacy that was enjoyed
in a wired environment.
Unfortunately, it failed miserably.
For a number of reasons, WEP is extraordinarily easy to crack because of a flawed implementation
of the RC4 encryption algorithm.
It's not unusual to be able to crack WEP in less than 5 minutes. This is because WEP used a very
small (24-bit) initialization vector
(IV) that could be captured in the datastream, and this IV could then be used to discover the
password using statistical techniques.
Despite this, I still find it being used in household and small business implementations, but
seldom in an enterprise environment.
- WPA -
WPA was the response by the industry to the revealed weaknesses of WEP. It's often referred to as WPA1 to distinguish it from WPA2. WPA used Temporal Key Integrity Protocol (TKIP) to improve the security of WEP without requiring new hardware. It still uses WEP for encryption, but it makes the statistical attacks used to crack WEP much more difficult and time-consuming.
- WPA2-AES -
WPA2-AES is the enterprise implementation of WPA2. It uses the Advanced Encryption Standard or AES to encrypt data and is the most secure. It's often coupled with a RADIUS server that is dedicated for authentication. Although cracking it is possible, it significantly more difficult.
Channels
Like our radio, wireless has multiple channels so that various communication streams don't
interfere with each other.
The 802.11 standard allows for channels ranging from 1 thru 14.
In the U.S., the FCC regulates wireless communication and devices for use in the states are only
enabled to use channels
1 thru 11. Europe uses channels 1 thru 13 and Japan 1 thru 14. Other nations may also use
the full range.
For the hacker, this can be useful information as a rogue AP using channel 12 thru 14 would be
invisible to U.S.-made wireless
devices and security professionals scanning for rogue access points.
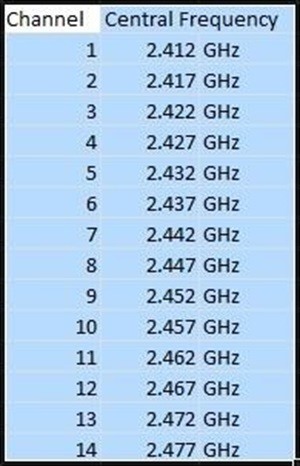
Each channel has a width of 22 Mhz around its central frequency. To avoid interference, an AP
can use any of these channels, but
to avoid any overlap, channels 1, 6, and 11 are most often utilized in the U.S. The other
channels can be used, but because
you need five channels between the working channels to not overlap signals,
with three or more channels, only 1, 6, and 11 will work.
Datagrams and Frames
An understanding of the structure of wireless datagrams is critical for successful wireless
hacking, but is beyond the scope
of this introduction. I will introduce some of this information when necessary in future
tutorials, but you may want
to take some time to study wireless frames and datagrams from other sources.
Signal Strength
In the U.S., the FCC regulates among other things, the strength of the wireless access point's
signal. The FCC says that the
access point's signal cannot exceed 27 dBm (500 milliwatts). Most access points have this limit
built-in, but we can change
and override this limitation, if the access point is capable of a stronger signal. This may be
useful for
the hacker in setting up evil twins and rogue access points where strength of signal is
critical, among other techniques.
Aircrack-ng
For nearly all of our Wi-Fi hacking, we will be using aircrack-ng which is included in Kali
Linux. Even in those hacks where
we use other tools such cowpatty or reaver, we will use the aircrack-ng suite of tools for some
part of the hack,
so we need to become familiar with it.
WiFi Adapters
One of the crucial needs to becoming an effective Wi-Fi hacker is the Wi-Fi adapter. Generally,
the Wi-Fi adapter on your
laptop or desktop is insufficient for our purposes. The key capability we need is the ability to
inject packets into the
access point and most run-of-the-mill wireless adapters are incapable of packet injection.
Aircrack-ng has a list of
Wi-Fi adapters that can work with their suite of tools.
That having been said, I highly recommend Alfa AWUS036NH USB wireless adapter. This is what I
use.
It's available from several locations for between $30 to $50.

It does everything I need, is fast, has an external antenna, is recognized by BackTrack, and
automatically loads its drivers.
In addition, it comes in 1000mw and 2000mw versions. That can be critical in rogue access point
hacks, despite the
fact that the FCC limits signal strength the 500mw.
Antennas
Antennas come in two basic types, omni-directional and directional. Most APs and wireless
adapters come
with omni-directional antennas, meaning that they send and receive in all directions.
The Alfa card that I recommend comes with an external antenna that is omni-directional, but has
a gain of 5dBi
(gain is a measure when applied to antennas, of how much the antenna can increase the signal).
This means that it can increase the signal by focusing the signal similar to that of a
reflector on a flashlight. In addition, it can change position to better receive particular
signals as well as a cable and suction cup adapter for mounting on a wall or window.

Directional antennas can also be useful for hacking when attempting to focus your exploits to a
remote access point.
The literature contains references to Wi-Fi signals that have been sent and received over 100
miles or about 160km
using directional antennas. For most commercial directional antennas, you can expect to be able
to pick up wireless
communication up to 4km or 2.4 miles.
These can be obtained from a variety of sources usually for under $100 with a gain of between
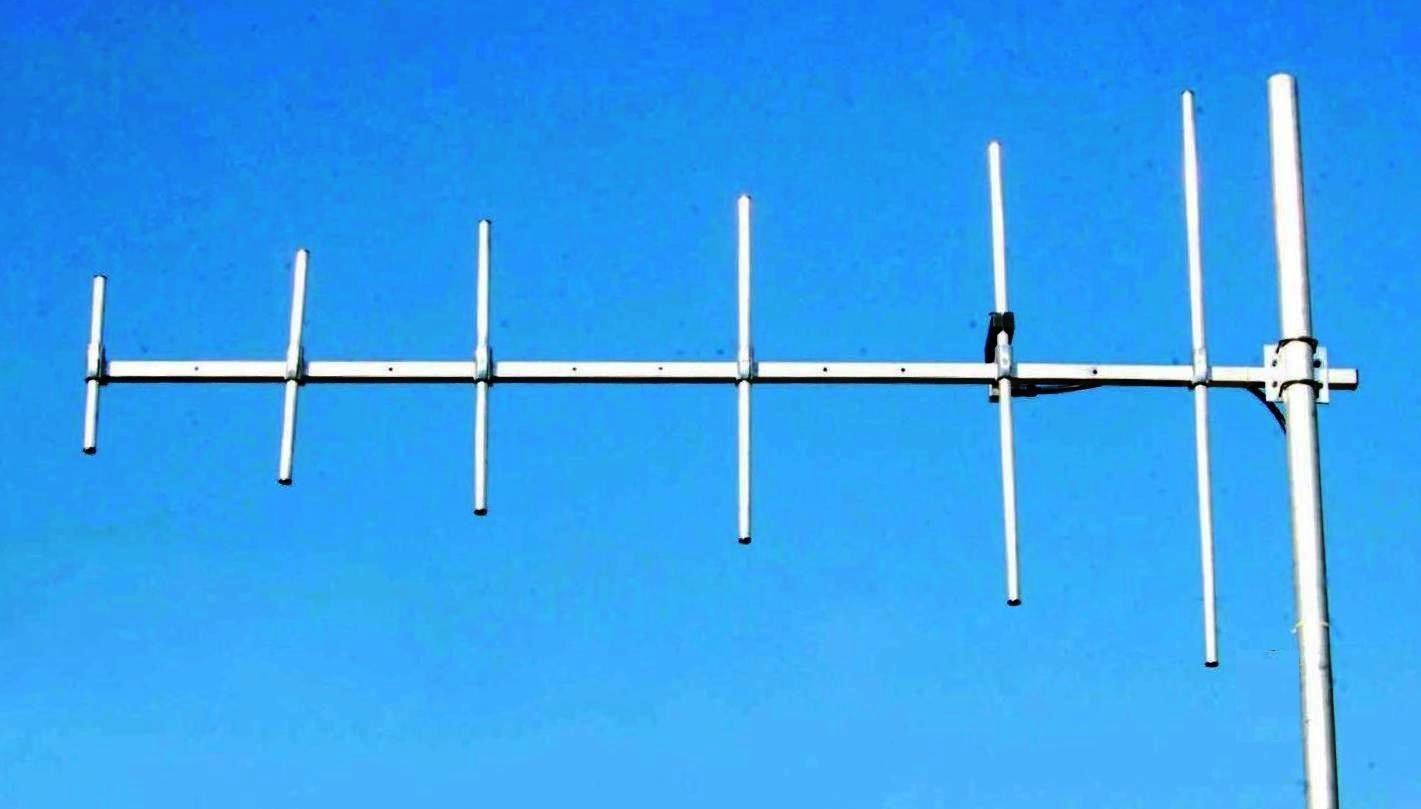
15dBi and 20dBi. A Yagi antenna
is an example of a directional antenna that is often used in hacking wireless over significant
distances.
Now that you know the terminology and basics, lets get started.....
